Network security
Paloalto
The Zero Trust Network Security Platform secures a world where any user can work anywhere-without restrictions. Zero Trust, including enabling secure access for all users irrespective of location, inspecting all traffic, enforcing policies for least-privileged access control, and detecting and preventing advanced threats. This significantly reduces the pathways for adversaries, whether they are inside or outside your organization, to access your critical assets. it supports Hardware Appliances (PA-Series), Virtual Appliances (VM-Series) and Secure Access Service Edge (SASE). Next Generation Firewall Palo Alto can increase capabilities with cloud security service such as Adv TP, Adv WF, Adv URL, DNS Security, etc.

Fortinet
Network Firewall
FortiGate is the most deployed network firewall with over 50% of global market share. FortiGate Next-Generation Firewalls (NGFWs) protect data, assets, and users across today’s hybrid environments. Built on patented Fortinet security processors, FortiGate NGFWs accelerate security and networking performance to effectively secure the growing volume of data-rich traffic and cloud-based applications. FortiGate NGFWs, backed by FortiGuard AI-Powered Security Services, help you prevent cyberattacks and mitigate security risks with consistent, real-time protection and responses against even the newest and most sophisticated threats.
AI-Powered Security
AI-centric threat intelligence offers timely protection, proactive defense, and streamlined operations
Optimal Energy Efficiency
Patented ASICs help create sustainable, scalable networks with faster security processing
Simplified Operations
Unified management reduces network complexity and automates security posture across all edges
Better User Experience
Integrated SD-WAN enables simplified orchestration and secure interconnection among offices
Secure Access from Anywhere
Built-in ZTNA capabilities enforce secure access for users anywhere to applications and infrastructure
Lower TCO Across Use Cases
Flexible and rich portfolio with Wi-Fi, LTE, PoE, DSL, bypass, ruggedized models for any requirement
Log management | SIEM
Fortinet
Delivering on the Promise of Next-Gen SIEM
FortiSIEM is designed to be the backbone of your security operations team and is your ultimate defense against attacks. It includes a unique, high-performance IT/OT SIEM feature-set built on advanced analytics, a fully inbuilt configuration management database (CMDB), native SOAR automation, and GenAI assistance.
Product Demo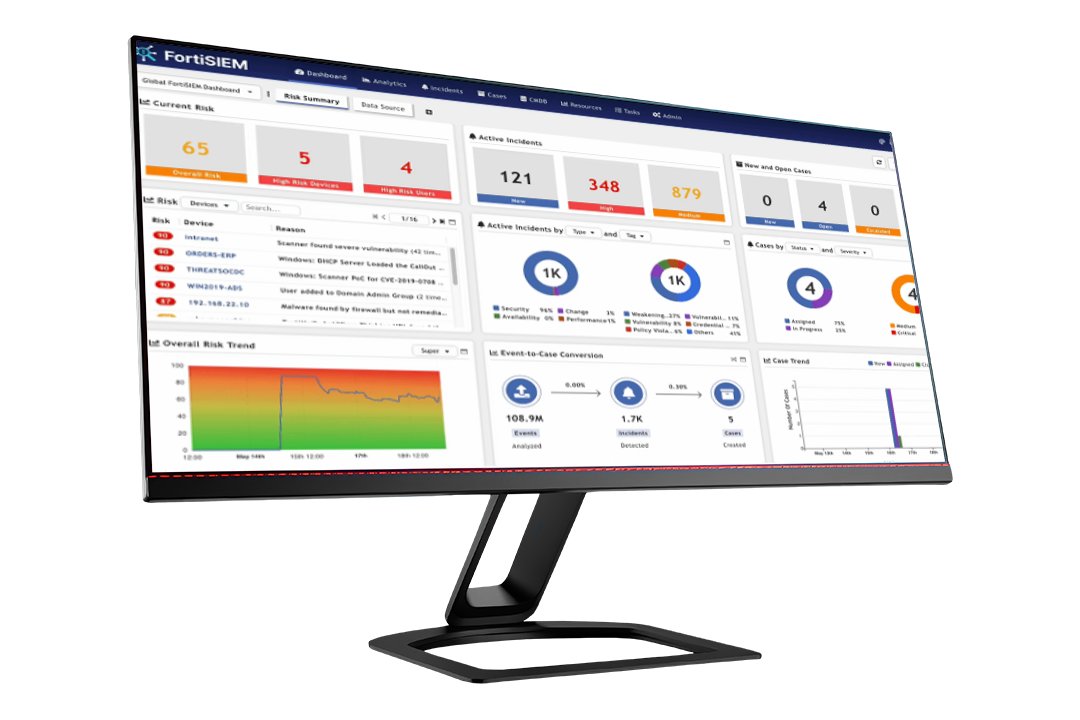
Next-Generation SIEM Platform
FortiSIEM truly delivers next-gen SIEM with enterprise-wide IT/OT event collection, advanced detection analytics, a rich user experience, and a unique CMDB, all powered by the latest in automation and AI. Delivering out-of-the-box value, complete flexibility, and ultimate scale, it’s the ideal solution for organizations of any size.
View moreNetevid
Compliance and Audit
System Logging of NetEvid perform ITIL framework compliance which define by
- User Authentication
- Authentication privilege level
- Access History Records
- Events records in changes, failure, and errors Distributor
- Records all systems structure changes
Key Features
- Universal Centralize Log Management to compliance requirements
- Fully integrated and extremely fast for log collection
- Log indexing for fast log searching
- Support Log retention and search up to 1 year
- Highly Log secured with SHA-256 Hashing and Archive
- Customizable and Open for predefine report management
- Support Web GUI and Command Line (CLI)
- Role Based Access Control according to Authentication permit
- Flexible and Hybrid for Log forwarding application
- Support External Backup or Network Storage
- Power searching through multiple search conditions

Vulnerability assessment
Tenable nessusView more
Unlimited vulnerability assessments you can use anywhere
Know
your vulnerabilities
Automate point-in-time assessments to identify software flaws, missing patches, malware and misconfigurations across a variety of operating systems, devices and applications.
Expose
the threats that matter
Nessus provides a variety of vulnerability
scoring systems like CVSS v4, EPSS
and Tenable’s VPR to help you
implement effective vulnerability
prioritization for remediation efforts.
Close
knowledge gaps
Get actionable tips and tricks
on the next steps to take with a
resource center that can guide
experienced and non-security staff.
Endpoint
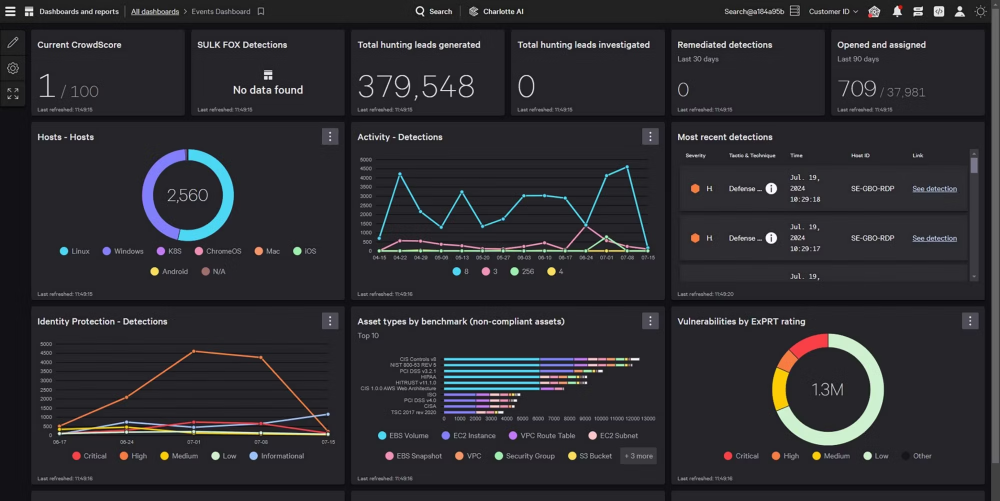
CrowedstrikeView more
The leader in endpoint security
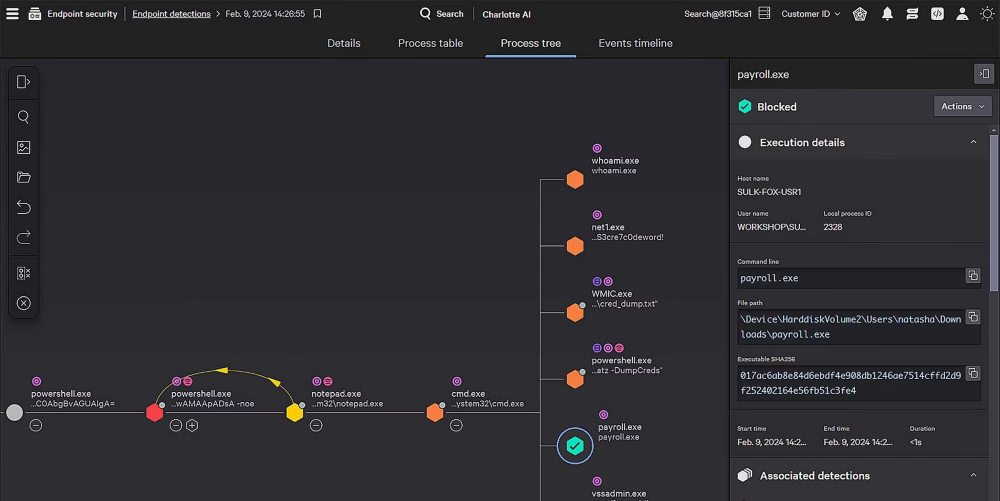
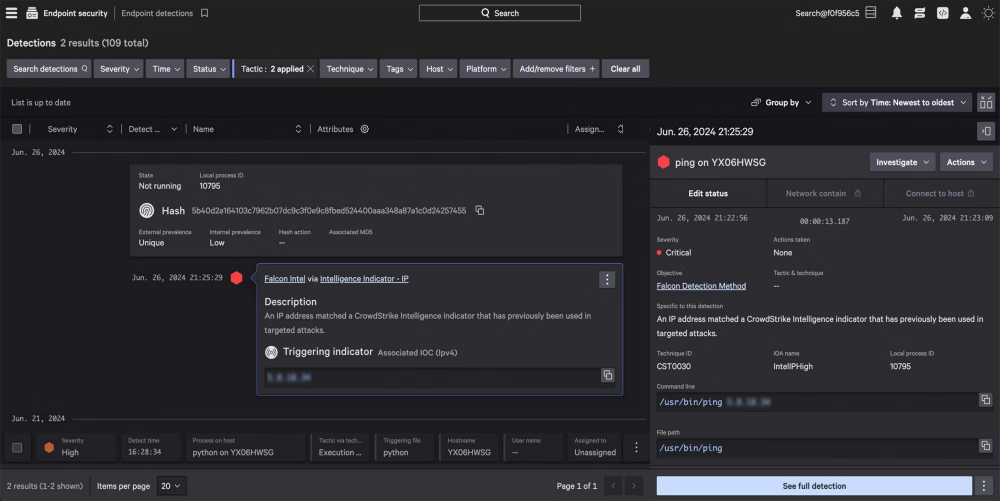
Only CrowdStrike combines AI-powered detection, adversary intelligence, and pioneering indicators of attack to identify and stop modern attacks — catching ransomware, lateral movement, and stealthy intrusions alike.
Stop cross-domain attacks
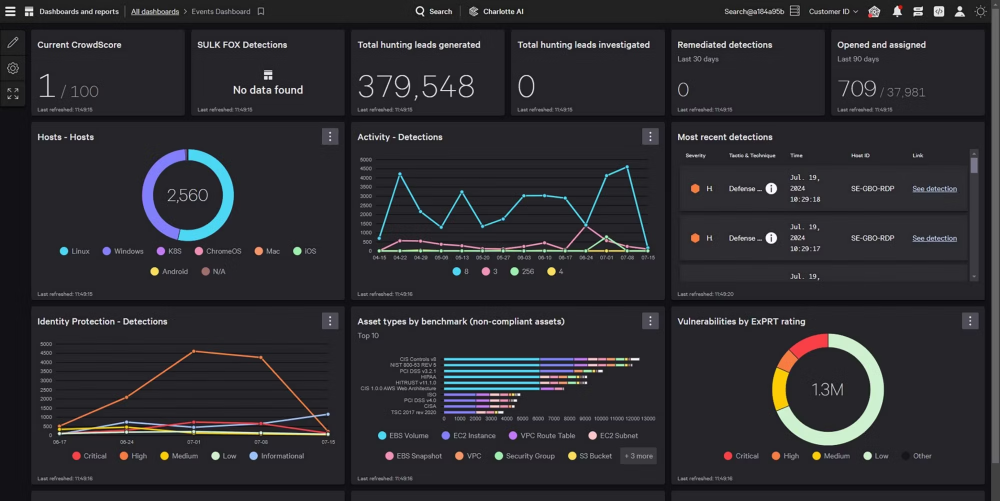
CrowdStrike extends protection beyond endpoints, unifying visibility across the CrowdStrike Falcon® platform to expose hidden threats that siloed tools miss. Expand protection with 10GB/day of third-party data ingest free via CrowdStrike Falcon® Next-Gen SIEM.
Precision detection meets autonomous response
CrowdStrike pioneered EDR to quickly stop advanced attacks. Our adversary-driven approach delivers precise, context-rich detections, while agentic AI automates detection triage, investigations, and response — cutting MTTR from hours to minutes.
One agent. Zero complexity. Full coverage.
Skip the complexity and tool sprawl. CrowdStrike’s single lightweight agent deploys in minutes and protects every major operating system, delivering instant security, fleet-wide visibility, and seamless scale.
AI that transforms security operations
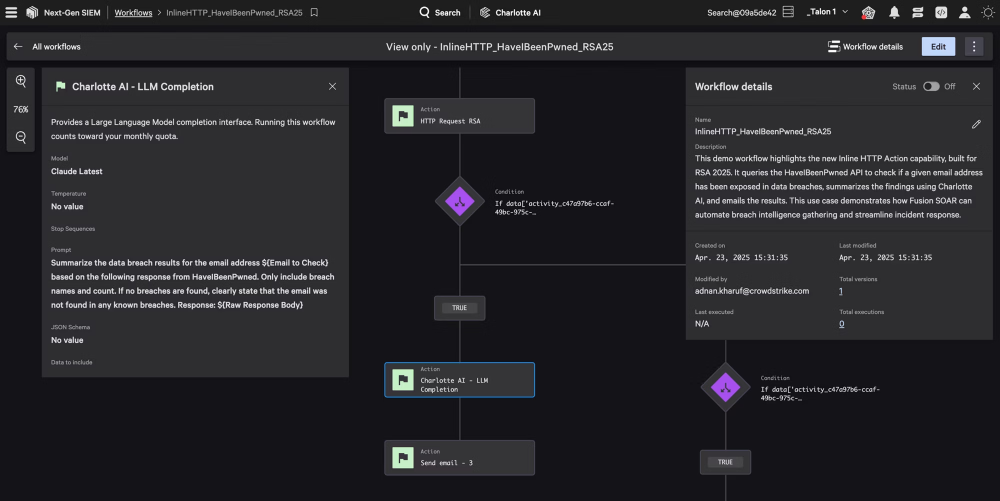
CrowdStrike® Charlotte AI™ uses generative and agentic AI to act with the instincts of a seasoned analyst — crafting queries, building workflows, and responding autonomously with accuracy and speed. It’s like having your best security analyst on every alert, 24/7.
TrendMicroView more
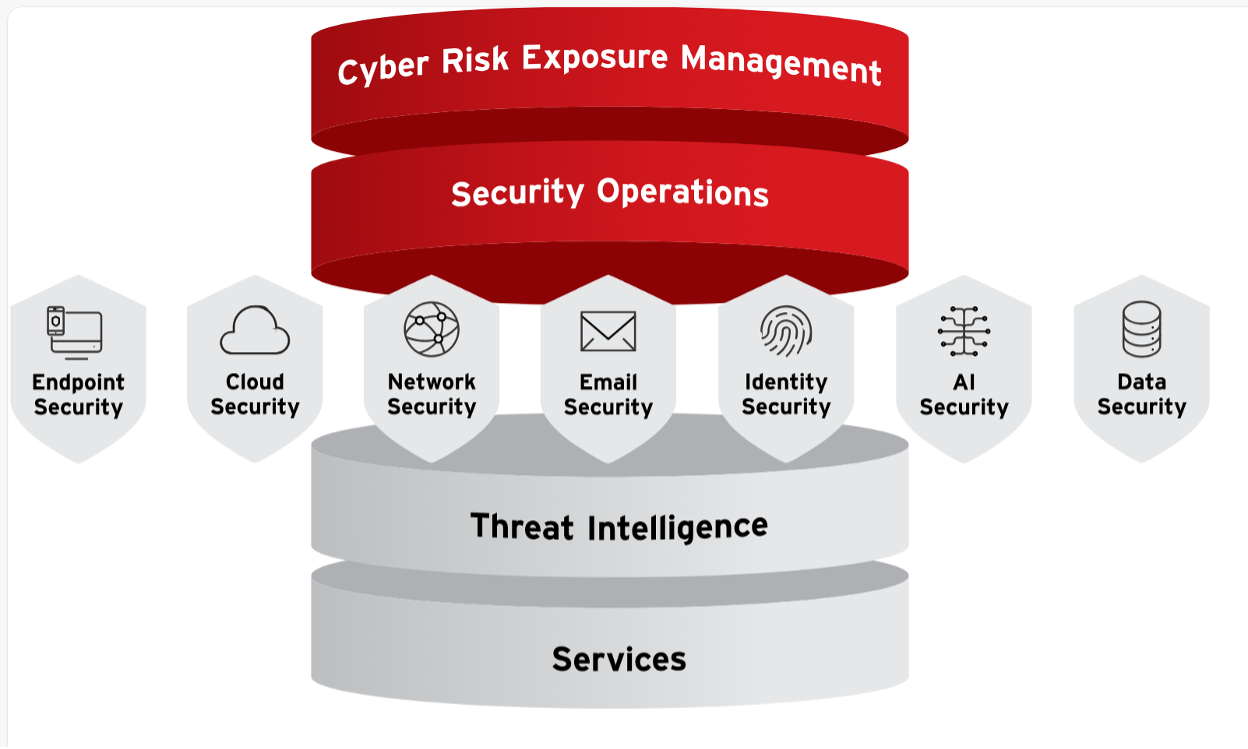
Proactive security starts here
Trend Vision One is the only enterprise cybersecurity platform that centralizes cyber risk exposure management, security operations, and robust layered protection – empowering you to predict and prevent threats, accelerating proactive security outcomes.
Visibility
Eliminate security blind spots with a comprehensive view of your entire digital estate.
Prioritization
Focus on what matters most – our platform evaluates and ranks security issues based on business impact and urgency.
Mitigation
Elevate security into a strategic partner for innovation by moving beyond reactive threat response toward strategic risk management to support the business.
Supercharge your defense with the first proactive cybersecurity AI
Seamlessly integrated with Trend Vision One™, Trend Cybertron – the industry’s first proactive cybersecurity AI – empowers you to stay ahead of threats and eliminate gaps before they’re exploited. It combines specialized AI to detect, predict, and prevent attacks, maximizing the impact of your security operations. Backed by 35 years of threat intelligence and 20 years of AI innovation, it enables you to take a truly proactive stance against today’s most sophisticated cyber risks.